News
Developers Again Blamed for Cloud Back-End Security Vulnerabilities
- By David Ramel
- June 5, 2017
Developers are once again being blamed for cloud back-end security vulnerabilities, this time in a new report from Appthority.
The company published investigation results that found nearly 43 TB of enterprise data was exposed on cloud back-ends, including personally identifiable information (PII). This comes just shortly after a similar report from a different security company.
In the new "2017 Q2 Enterprise Mobile Threat Report" report (free upon providing registration info), Appthority found "data leakage" from mobile apps that send data to unsecured cloud back-ends. While security concerns typically focus on a triad of other factors -- apps, device threats and network threats -- this data leakage on the back-end was dubbed the "HospitalGown" threat because of that garment's open back-end.
"In total, we found almost 43 TB of data exposed and 1,000 apps affected by the HospitalGown vulnerability," Appthority said in a blog post last week. "Looking at a subset of 39 apps, we still found 280 million records exposed, a total of about 163 GB of data. This is a staggering amount of leaked information, and in some cases represents the entirety of customer or operational data for an enterprise."
The report echoes the findings of an earlier report by RedLock Inc., which revealed many security issues primarily caused by user misconfigurations on public cloud platforms. RedLock claimed it found 82 percent of hosted databases remain unencrypted, among many other problems.
As with the RedLock report, developers were blamed for the HospitalGown vulenerabilities. "HospitalGown is a vulnerability to data exposure caused, not by any code in the app, but by the app developers' failure to properly secure the back-end (hence its name) servers with which the app communicates and where sensitive data is stored," Appthority said.
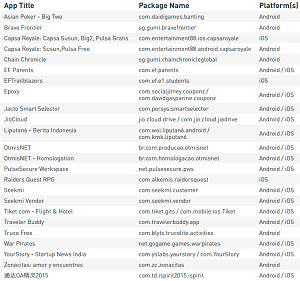 [Click on image for larger view.]
Sample of Vulnerable Apps with Exposed Elasticsearch Servers (source: Appthority)
[Click on image for larger view.]
Sample of Vulnerable Apps with Exposed Elasticsearch Servers (source: Appthority)
Unsecured Elasticsearch servers and MongoDB databases were prime targets of a series of ransomware attacks earlier this year that generated widespread publicity in the security field. However, that publicity apparently wasn't enough to significantly alleviate the issue.
"As our findings show, weakly secured back-ends in apps used by employees, partners and customers create a range of security risks including extensive data leaks of personally identifiable information (PII) and other sensitive data," the report states. "They also significantly increase the risk of spear phishing, brute force login, social engineering, data ransom, and other attacks. And, HospitalGown makes data access and exfiltration far easier than other types of attacks."
Key findings of the report as listed by the company include:
- Affected apps are connecting to unsecured data stores on popular enterprise services, such as Elasticsearch and MySQL, which are leaking large amounts of sensitive data.
- Apps using just one of these services revealed almost 43TB of exposed data.
- Multiple affected apps leaked some form of PII, including passwords, location, travel and payment details, corporate profile data (including employees' VPN PINs, emails, phone numbers), and retail customer data.
- Enterprise security teams do not have visibility into the risk due to the risk's location
in the mobile app vendor's architecture stack.
- In multiple cases, data has already been accessed by unauthorized individuals and ransomed.
- Even apps that have been removed from devices and the app stores still pose an exposure risk due to the sensitive data that remains stored on unsecured servers.
The company said its Mobile Threat Team identified the HospitalGown vulnerabilities with a combination of its dynamic app analysis tool and a new back-end scanning method, looking at the network traffic on more than 1 million enterprise mobile apps, both iOS and Android.
As with the misconfiguration problems identified in the RedLock report, Appthority emphasized that all cases of HospitalGown vulnerabilities were caused by human errors, not malicious intent or inherent infrastructure problems.
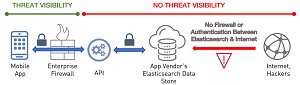 [Click on image for larger view.]
Unsecured Mobile Back-End With API: Pulse Secure Case Study (source: Appthority)
[Click on image for larger view.]
Unsecured Mobile Back-End With API: Pulse Secure Case Study (source: Appthority)
That human error was especially prevalent in two app implementations investigated by Appthority: Pulse Workspace (for accessing enterprise network and Web applications) and Jacto apps (from an agricultural machinery company).
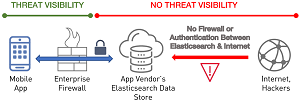 [Click on image for larger view.]
Unsecured Mobile Back-End No API: Jacto Case Study (source: Appthority)
[Click on image for larger view.]
Unsecured Mobile Back-End No API: Jacto Case Study (source: Appthority)
Appthority also provided some tips for enterprises to protect themselves from HospitalGown threats:
- Maintain a list of active apps and vendors so you know who has access to your data, particularly the sensitive data. Remove apps from your environment that may continue to store or access sensitive data when no longer in use. This applies not only to BYOD apps that employees download onto their devices, but to enterprise sanctioned apps that are available via an enterprise app store or Enterprise Mobility Management (EMM) platform.
- Review your current mobile app inventory immediately. If anyone in your enterprise environment is using the Pulse Workspace app, update to the latest app version immediately. If anyone in your enterprise environment is using the Jacto Smart Selector, OtmisNET, or OtmisNET - Homologation apps or any of the apps listed in Appendix A [the figure displayed above], contact the app developer immediately to request secure encryption of your data.
- Contact any vendors for which your enterprise uses a mobile app. Ask them for a letter from their legal department that confirms their app's back-end is secured following best practices for the backend platform. Request that they limit the amount of personal information or site credentials stored on backend databases to the minimum needed for app functionality, and protect the data via encryption.
Appthority said it disclosed information about the exposed data to app developers and to affected providers, such as AWS.
"In some cases, the issues were remediated immediately," the company said. "Unfortunately, in others, we received no response and the data is still exposed."
About the Author
David Ramel is an editor and writer at Converge 360.