News
After MongoDB Debacle, Expect More Ransomware, Open Source Attacks in 2017
- By David Ramel
- January 19, 2017
After the recent MongoDB debacle in which tens of thousands of unsecured open source databases were hijacked for ransom, security specialists are predicting more of the same for 2017.
As we reported earlier this month, older MongoDB databases were left open in a default configuration setting. Although MongoDB Inc. fixed the flaw, many of the older implementations remained online. After a hacker exploited the vulnerability by deleting an online database's contents and demanding a ransom in Bitcoin from the owner, many other hackers recognized the opportunity and piled on, reportedly hijacking more than 27,000 databases.
After that initial spate of attacks, the hackers moved on to Elasticsearch servers and other databases.
Just yesterday, for example, Bleeping Computer reported new attacks on CouchDB and Hadoop databases, sometimes for ransom, sometimes just to delete data -- cyber vandalism.
Although these much-publicized attacks concerned only a few types of databases, they serve as a sobering reminder of the vulnerabilities in open source software, where it's often incumbent upon users to secure the open source components they use in projects.
Mike Pittenger, an exec at open source security specialist Black Duck Software Inc., predicts that cyber attacks leveraging known open source vulnerabilities will increase by 20 percent in the new year.
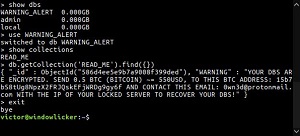 [Click on image for larger view.]
A MongoDB Ransom Note (source: Victor Gevers, via Twitter, )
[Click on image for larger view.]
A MongoDB Ransom Note (source: Victor Gevers, via Twitter, )
In outlining his top four open source security predictions in a Compare the Cloud article last week, Pittenger outlined several characteristics of open source software that make it an attractive target. They include:
- Open source use is ubiquitous, and therefore offers a target-rich environment.
- Open source vulnerabilities are publicly disclosed in the National Vulnerability Database (NVD), and references are often made to exploits that "prove" the vulnerability.
- The support model for open source is usually the opposite of commercial software. For the latter, a service level agreement is typically in place that requires the vendor to "push" updates to its customers and notify them of security issues. With open source, users have elected to download the component and comply with its license. They also take responsibility for monitoring the project for updates, including security issues, and deciding whether or not to "pull" the updates.
Pittenger's second prediction followed along the same lines: "In 2017 we will continue to see high-profile, high-impact breaches based on open source vulnerabilities disclosed years previously, such as Heartbleed, Shellshock and Poodle."
"Black Duck's Open Source Security Audit Report found that, on average, vulnerabilities in open source components used in commercial application were over 5 years old," Pittenger said. "The Linux kernel vulnerability discovered 8/16 (CVE-2016-5195) had been in the Linux code base since 2012. Most organizations don't know about the open source vulnerabilities in their code because they don't track the open source components they use, and don't actively monitor open source vulnerability information."
Meanwhile, McAfee Labs made a 2017 prediction about increased ransomware incidents last November, even before the MongoDB attacks were publicized. The firm sees denial-of-service ransom attacks becoming common against cloud service providers and other cloud-based organizations. Also, it sees ransomware emerging as the primary threat to Internet of Things (IoT) implementations.
However, on the "good news" front, McAfee sees ransomware attacks decreasing in the second half of the year.
"Ransomware will remain a very significant threat until the second half of 2017," the company said in its "2017 Threats Predictions" report. "Ransomware-as-a-service, custom ransomware for sale in dark markets, and creative derivatives from open-source ransomware code will keep the security industry busy through the first half of the year. Ransomware's impact across all sectors and geographies will force the security industry to take decisive actions. We predict that initiatives like the No More Ransom! collaboration, the development and release of antiransomware technologies, and continued law enforcement actions will reduce the volume and effectiveness of ransomware attacks by the end of 2017."
That will be too late for many MongoDB database owners, of course. For those MongoDB DBAs and others worried about falling prey to similar attacks, there are plenty of sources of advice and guidance, including:
The same holds true for open source software security in general, also:
As Pittenger noted, however, securing open source systems against cyber attacks won't be easy in the coming year.
"Organizations of all sizes and types are expanding their use of cloud and mobile applications, which rely heavily on open source components; and these software elements live outside the company firewall," he said. "Hackers have learned that applications are the weak spot in most organizations' cyber security defenses and widely available open source vulnerability exploits have a high ROI, allowing them to compromise thousands of sites, applications and IoT devices with minimal effort."
About the Author
David Ramel is an editor and writer at Converge 360.