MongoDB Ransom Notes: Humor, Bad Spelling, Not Much Style
With phrases like, "We are so sorry," and, "wtf were you thinking," ransomware notes from the recent deluge of database hijackings came in all styles, shapes and sizes.
However, it looks like the quality of ransom notes really went downhill when the script kiddies got wind of the wide-open gold (or rather, Bitcoin) mine and piled on after the late-December MongoDB attacks were first publicized. Some exhibited absolutely no sense of style or even decent formatting (doesn't readability count in criminal ransom notes anymore?) and were rife with bad spelling and grammar mistakes.
Seriously, kids, if you're going to go through the trouble of hijacking someone's valuable data and demand money to get it back, can't you at least use a little flair, a certain "je ne sais quoi"? (I know, kids -- you might have to use a dictionary to follow along here.) I mean, "pwned" really isn't cool anymore.
Anyway, for some Friday fun (and perhaps a little distraction from some other bad things going on this Jan. 20), here's a look at the different styles of ransom notes that started with unsecured MongoDB databases and moved on to CouchDB, ElasticSearch, Hadoop and who knows what else.
(Special thanks to Victor Gevers, who, along with Niall Merrigan, has been instrumental in tracking these attacks on Twitter, for supplying most of these images. Note that Gevers credited Toufik Airane for first tweeting about the MongoDB hijackings.)
From what I can tell, the image below depicts the first ransom note published by Gevers on his Twitter feed, just a couple days after Christmas. It's short and to the point, but "harak1r" did commit the cardinal Internet sin of SHOUTING most of his message. And, if you want to be real picky, he should've closed up the space between the text and exclamation mark.
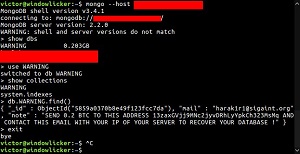 [Click on image for larger view.]
An Early Note (source: Twitter)
[Click on image for larger view.]
An Early Note (source: Twitter)
Later on, the hackers got wordier -- and funnier ("wtf were you thinking?"). Note in the image, below, though, the bad spelling ("publically" instead of "publicly" and "restoreable" instead of "restorable"), along with bad grammar, punctuation and sentence structure. (Maybe think about going back and getting your GED, sonny.)
The semi-apologetic "We are not animals" (no, we're just criminal extortionists) and polite tones are nice touches, though.
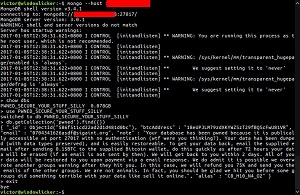 [Click on image for larger view.]
"wtf were you thinking?" (source: Twitter)
[Click on image for larger view.]
"wtf were you thinking?" (source: Twitter)
Talk about bad spelling. Check out the image below. Proof of "paiement," really? That's such an egregious (look the word up, junior) spelling error I'm wondering if it's on purpose. But, in light of verbiage such as, "your IP of your server," it's probably just another moron hacking in from his parents' basement. Then again, it looks like this miscreant just copied that line from the first note depicted above, complete with the SHOUTING, tsk, tsk. Is it really too much to work up your own ransom note?
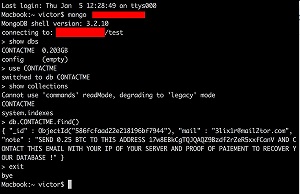 [Click on image for larger view.]
"proof of paiement" (source: Twitter)
[Click on image for larger view.]
"proof of paiement" (source: Twitter)
The note below has a bunch of weird capitalization mistakes, but at least contains a little sardonic humor ("You are welcome!"). Gee, thanks!
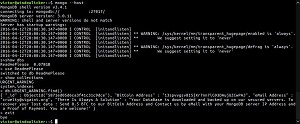 [Click on image for larger view.]
"You are welcome!" (source: Twitter)
[Click on image for larger view.]
"You are welcome!" (source: Twitter)
Granted, the styling capabilities of these and other notes from the recent spate of attacks were limited, as there's apparently only so much you can do with this delivery mechanism. But, surely, if these people are technically proficient enough to extort money without getting caught, they could figure out how to jazz up their ransom notes.
Take the images below, for example. Different scenarios altogether, but they really show off what can be done with a ransom note once the bad guys get organized and start paying attention to details.
Note the use of color, graphics and typography. The helpful links for useful information. The ominous countdown clocks that inject a sense of urgency. The obvious calls to action. The design balance. Sure, there are all kinds of punctuation and spacing mistakes and such, but they just feel right, imparting a sense of foreboding and danger.
Now that's how to do ransom notes!
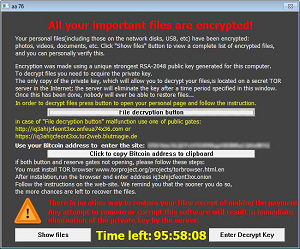 [Click on image for larger view.]
TeslaScript Ransom Note (source: How to solve tech issues)
[Click on image for larger view.]
TeslaScript Ransom Note (source: How to solve tech issues)
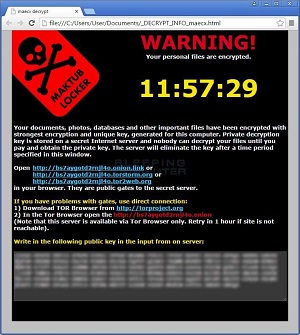 [Click on image for larger view.]
Maktub Locker Ransom Note (source: Neowin)
[Click on image for larger view.]
Maktub Locker Ransom Note (source: Neowin)
What ingredients do you think make up a good ransom note? Please share your thoughts here in the comments section or drop me a line.
Posted by David Ramel on January 20, 2017