News
Google's Fuzz Tester IDs Hundreds of Potential Open Source Security Flaws
- By David Ramel
- May 15, 2017
The sorry state of open source security was further revealed by Google, which reported its fuzz testing tool has found hundreds of potential security vulnerabilities. The company also announced a reward program for developers who help out with its fuzz testing program.
Google launched its OSS-Fuzz testing tool five months ago in an effort to help make the open source software arena more secure and stable. Wikipedia describes fuzz testing as "an automated software testing technique that involves providing invalid, unexpected or random data as inputs to a computer program."
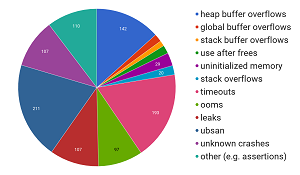
The cloud giant put its tool to work by processing some 10 trillion such test inputs a day with the help of the open source community, which integrated the tool into 47 projects. In the five months of work, the tool has discovered more than 1,000 bugs, of which 264 could be potential security vulnerabilities.
"OSS-Fuzz has found numerous security vulnerabilities in several critical open source projects: 10 in FreeType2, 17 in FFmpeg, 33 in LibreOffice, 8 in SQLite 3, 10 in GnuTLS, 25 in PCRE2, 9 in gRPC, and 7 in Wireshark, etc.," the company said in a blog post last week. "We've also had at least one bug collision with another independent security researcher (CVE-2017-2801). (Some of the bugs are still view restricted so links may show smaller numbers.)"
 [Click on image for larger view.]
A Breakdown of the Type of Bugs Being Found (source: Google)
[Click on image for larger view.]
A Breakdown of the Type of Bugs Being Found (source: Google)
The new report is but the latest in a string of research studies that have shed light on security vulnerabilities in open source software.
Last month, for example, German researchers published a paper finding that developers who copy and paste code directly into their open source software can introduce security vulnerabilities if that code comes from flawed online tutorials.
Also, Black Duck Software Inc. recently revealed the results of security audits it undertook that show "widespread weakness in addressing open source security vulnerability risks."
And earlier this month, other researchers -- these at the University of Michigan -- published a paper in which they broke new ground in investigating security implications of open Internet ports in Android apps, finding flawed apps that leave millions of users vulnerable to attack.
To improve this situation, Google also announced new rewards for developers who help make open source software more secure by participating and adopting the ideal integration guidelines that the company established for its OSS-Fuzz tool.
"To qualify for these rewards, a project needs to have a large user base and/or be critical to global IT infrastructure," Google said. "Eligible projects will receive $1,000 for initial integration, and up to $20,000 for ideal integration (the final amount is at our discretion). You have the option of donating these rewards to charity instead, and Google will double the amount."
In order to qualify for the ideal integration reward, Google said projects must show that:
- Fuzz targets are checked into their upstream repository and integrated in the build system with sanitizer support (up to $5,000).
- Fuzz targets are efficient and provide good code coverage (more than 80 percent) (up to $5,000).
- Fuzz targets are part of the official upstream development and regression testing process, that is, they are maintained, run against old known crashers and the periodically updated corpora (up to $5,000).
- The last $5,000 is a "l33t" bonus that Google may reward at its discretion for projects that it believes have gone the extra mile or done something really awesome.
Developers can apply for that program here.
About the Author
David Ramel is an editor and writer at Converge 360.