News
Vulnerable Mobile, IoT Code Caused by 'Rush to Release' Says Security Report
- By David Ramel
- February 9, 2017
"Rush to release is the main reason why both mobile and IoT apps contain vulnerable code," says a new Ponemon Institute LLC security research report.
Furthermore, these risks are increased by an emphasis on end-user convenience over security, and organizations lack urgency to address threats.
Those are but a few key findings in the "2017 Study on Mobile and Internet of Things Application Security" report sponsored by IBM and security firm Arxan Technologies Inc.
While other studies have confirmed the "rush to release" problem in mobile app development and other areas (such as this and this), this new survey adds data on the relatively new but rapidly growing IoT space.
"The risks created by mobile apps have been well researched and documented," the report said. "This study reveals how companies are unprepared for risks created by vulnerabilities in IoT apps."
The survey polled 593 IT and IT security practitioners who are familiar with their organizations' security practices during the development of applications and devices.
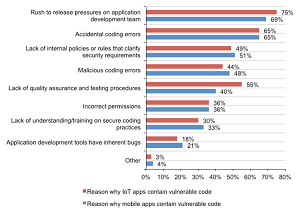
"Respondents acknowledge the risk of security vulnerabilities in both mobile and IoT apps," the study said. "However ... more respondents are likely to say IoT apps are harder to secure (84 percent) versus mobile apps (69 percent). Additionally, 55 percent of respondents say there is a lack of quality assurance and testing procedures for IoT apps."
 [Click on image for larger view.]
Causes of Vulnerable Mobile and IoT Code (source: Ponemon Institute)
[Click on image for larger view.]
Causes of Vulnerable Mobile and IoT Code (source: Ponemon Institute)
Concerning the persistent "rush to release" phenomenon, the report stated: "Sixty-nine percent of respondents say pressure on the development team is why mobile apps contain vulnerable code and 75 percent of respondents say the same reason contributes to vulnerable code in IoT apps. Accidental coding errors in mobile and IoT apps are another primary reason for vulnerable code (65 percent of respondents). An additional issue affecting the security of apps is the lack of internal policies or rules that clarify security requirements."
The persistence of the "rush to release" problem is exemplified by a previous Ponemon Institute study -- this one conducted in 2015 and titled "The State of Mobile Application Insecurity" -- that reached a similar conclusion. "65 percent of the participants in this study strongly agree that the security of mobile apps is sometimes put at risk because of expanding customer demand or need," it stated. "The 'rush to release' phenomenon challenges an organization's ability to address the risks of data leakage and malware."
Such findings closely mirror one found in a similar report conducted by F5 Networks Inc. last August, which didn't focus on mobile development. As we reported at the time: "67 percent of respondents say the 'rush to release' causes application developers in their organization to neglect secure coding procedures and processes."
Other key findings in the new Ponemon Institute report include:
- Testing of mobile and IoT apps is ad hoc, if done at all.
- Testing of mobile and IoT apps often does not occur until production.
- Broken cryptography and unintended data leakage are the most difficult mobile risks to mitigate.
- Malware is believed to pose a greater threat to mobile than IoT apps.
- Organizations have no confidence or are not confident they know all mobile and IoT apps in the workplace.
- Material data breach or cyber attacks have occurred and are reasons for concern.
- The functions most responsible for mobile and IoT security are outside the security function.
- Hacking incidents and regulations drive growth in budgets.
Compare those with some key findings from the 2015 Ponemon/IBM study that focused on mobile development:
- 50 percent of companies have zero budget for security apps.
- 40 percent of companies don't scan mobile app code for vulnerabilities.
- The average company security tests less than half of the apps it builds.
- 33 percent of companies never test apps for security.
To address such security problems, IBM said it had introduced cloud-based MobileFirst Protect Threat Management tool to its MobileFirst Protect offering. IBM said it automatically tracks suspicious activity on mobile endpoints and instantly stops device malware upon detection.
About the Author
David Ramel is an editor and writer at Converge 360.