News
Report Blasts Mobile Devs for Ignoring Known Security Flaws
- By David Ramel
- March 2, 2015
Mobile app developers failed to fix Secure Sockets Layer (SSL) vulnerabilities that were identified some five months ago, McAfee Labs said in its latest threat report.
The flaw that exposes man-in-the-middle (MITM) vulnerabilities to millions of users isn't being addressed even though developers were warned of them last September by the Computer Emergency Response Team (CERT) at Carnegie Mellon University, said McAfee, a security company acquired by Intel Corp. Even worse, it said, is that the flaw is easily fixed, but many developers just aren't bothering to do so.
CERT's "Vulnerability Note VU#582497" reported that "multiple Android applications fail to properly validate SSL certificates" on Sept. 3 last year.
"In January, McAfee Labs tested the 25 most popular apps on CERT's list of vulnerable mobile apps that send login credentials through insecure connections and found that 18 still have not been patched despite public disclosure, vendor notification, and, in some cases, multiple version updates addressing concerns other than security," the company said.
"McAfee Labs researchers simulated MITM attacks that successfully intercepted information shared during supposedly secure SSL sessions," the company continued. "The vulnerable data included usernames and passwords and in some instances, login credentials from social networks and other third-party services."
There's no proof of real-world exploits attacking the vulnerability, McAfee said, but so many apps have been downloaded that expose the flaw -- hundreds of millions, the company said -- that millions of users are at risk because of "the choice by mobile app developers to not patch the SSL vulnerabilities."
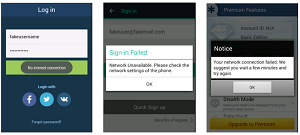 [Click on image for larger view.]
Some apps have addressed the SSL vulnerability, said McAfee, which illustrated how the apps display a network error message when an attack is underway.
[Click on image for larger view.]
Some apps have addressed the SSL vulnerability, said McAfee, which illustrated how the apps display a network error message when an attack is underway.
(source: McAfee Labs)
To prove its point, McAfee tested the most downloaded app exposing the flaw, a mobile photo editor that lets users share photos on social sites and cloud services. "We were able to intercept the app's username and password credentials entered to log into the cloud service to share and publish photos," the McAfee Labs Threats Report February 2015 states.
In a blog post last week, McAfee pointed out tips that users can follow to avoid MITM attacks and blasted developers for not addressing the vulnerability.
"But here's the thing with MITM attacks on both mobile and desktop devices," said McAfee's Gary Davis in the post. "They can be fixed fairly easily, but they often aren't. There is no good reason for this. Developers need to step up their security game and knock out any known vulnerabilities that could harm consumers."
Other findings in the 46-page report listed by McAfee include:
- Mobile malware samples grew 14 percent during the fourth quarter of 2014, with Asia and Africa registering the highest infection rates. At least 8 percent of all McAfee-monitored mobile systems reported an infection in Q4 2014, with much of the activity being attributed to the AirPush ad network.
- Potentially Unwanted Programs were detected on 91 million systems each day. McAfee Labs sees PUPs becoming more and more aggressive, posing as legitimate apps while performing unauthorized actions such as displaying unintended ads, modifying browser settings, or collecting user and system data.
- Beginning in Q3, the number of new ransomware samples began to grow again after a four-quarter decline. In Q4, the number of new samples grew 155 percent.
- After a brief drop in new malicious signed binaries, the pace of growth resumed in Q4 with a 17 percent increase in total signed binaries.
- McAfee Labs now detects 387 new samples of malware every minute, or more than six every second.
"Luckily, not all the news is bad," the report stated. "In the group of mobile apps with more than 10 million downloads, three apps identified as vulnerable by CERT last August have been fixed. All these apps show a network error when the MITM attack is in place."
About the Author
David Ramel is an editor and writer at Converge 360.