News
Study: Open Source Software Contributes to Mobile App Vulnerabilities
- By David Ramel
- September 13, 2018
A new study examined hundreds of popular Android apps for security vulnerabilities, finding that the improper use of open source software puts organizations and users at risk.
That risk includes the loss of key data or compromised privacy, said the American Consumer Institute Center for Citizen Research (ACI), a non-profit consumer education and research organization.
"We are calling on all apps developers to redouble their efforts to find vulnerable code and to use the latest patches to plug these security holes,” the ACI said in a statement this week.
The organization on Sept. 11 announced the publication of its report, "How Safe Are Popular Apps? A Study of Critical Vulnerabilities and Why Consumers Should Care" (available in a PDF here).
The report squarely puts the onus for increased mobile app security on developers using open source software with known vulnerabilities. The study examined the 330 most popular Android apps available on the Google Play Store. It found risks in apps from many trusted brands.
"Application developers need to invest the resources and institute processes for finding known security vulnerabilities in their code and patching them," the report said.
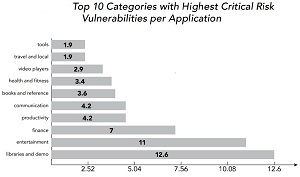 [Click on image for larger view.]
Top Risk Categories (source: ACI)
[Click on image for larger view.]
Top Risk Categories (source: ACI)
Key takeaways of the new report include:
- Of the sample of 330 apps, 32 percent or 105 apps were found to have security vulnerabilities with an average of 19 vulnerabilities per identified apps.
- Among the sample, 1,978 vulnerabilities were found across all severity levels with 43 percent of them being deemed as high risk or critical.
- Critical vulnerabilities were found in many common applications, including some of the most popular banking, event ticket purchasing, sports and travel apps.
The report builds upon numerous previous studies that reached similar conclusions. For example, security firm Black Duck last year found "widespread weakness in addressing open source security vulnerability risks" in an audit that it said "should be a wake-up call."
Apparently many developers haven't received that call. Shortly after that report, the sorry state of open source security was further revealed by Google, which reported its fuzz testing tool had found hundreds of potential security vulnerabilities.
We also reported on a study that linked flawed online tutorials to vulnerable open source software and yet another examination on the risks to enterprise software resulting from the use of open source.
Now, as then, the organization behind the report is repeating the call for more developer due diligence.
"It is recommended that Android app developers scan their binary files to ensure that they catch and address all known security vulnerabilities," the ACI said.
The ACI itself cited that 2017 Black Duck report, noting that while open source software by itself is no less secure than custom software, it exhibits certain characteristics that make its vulnerabilities attractive to hackers:
- Open source is widely used in commercial applications, providing attackers with a target-rich environment.
- Unlike some commercial software for personal computers and smartphones, where updates are automatically “pushed” to users, IoT devices and smartphones leverage a “pull” support model, where users are responsible for keeping track of vulnerabilities as well as fixes and updates for the software they use.
- If an organization is not aware of all the open source used in its code, it cannot properly defend against common attacks targeting known vulnerabilities.
- Hackers can more easily exploit known open source security vulnerabilities because they are publicly published on the CVE database, providing a roadmap for exploiting code.
In yet another "wake-up call" type warning, the ACI concluded: "Before government regulators intervene, application developers should take immediate, proactive steps to patch their applications that contain open source components and notify consumers when software updates are available. The potential for serious damage will only increase as open source code becomes even more widely used. The time to act is now."
About the Author
David Ramel is an editor and writer at Converge 360.