News
Google, IBM and Lyft Open Source Microservices Project
- By David Ramel
- May 24, 2017
The microservices approach to software development -- chaining together loosely coupled services to create larger applications -- just got a boost from Google, IBM and Lyft.
The companies today announced Istio, an open platform designed to help developers connect, manage and secure separate networks of microservices.
The three companies teamed up to consolidate earlier work they've done in order to improve traffic flow management and access policy enforcement, along with providing telemetry data aggregation between microservices -- all without changing existing code.
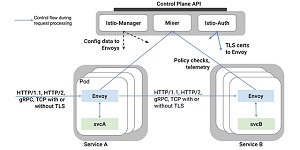
Those microservices can come from any vendor or source. Istio converts them into an integrated service mesh through the use of a new programmable routing and a shared management layer.
Through further environment support is planned, Istio runs on Kubernetes-based platforms, including the IBM Bluemix Container Service.
The new Istio Web site featured a blog post today introducing the project.
"Google, IBM and Lyft joined forces to create Istio from a desire to provide a reliable substrate for microservice development and maintenance, based on our common experiences building and operating massive scale microservices for internal and enterprise customers," the post said. "Google and IBM have extensive experience with these large scale microservices in their own applications and with their enterprise customers in sensitive/regulated environments, while Lyft developed Envoy to address their internal operability challenges. Lyft open sourced Envoy after successfully using it in production for over a year to manage more than 100 services spanning 10,000 VMs, processing 2M requests/second."
 [Click on image for larger view.]
Istio Reportedly Improves Visibility into Data Flows Among Apps (source: IBM)
[Click on image for larger view.]
Istio Reportedly Improves Visibility into Data Flows Among Apps (source: IBM)
Istio reportedly provides benefits such as:
- Intelligent routing and load balancing for HTTP, gRPC and TCP traffic
- Fine-grained control of traffic behavior with rich routing rules
- Resilience across languages and platforms
- Secure service-to-service authentication, traffic encryption and strong identity assertions
- Fleet-wide policy enforcement via a pluggable policy layer and configuration API supporting access controls, rate limits and quotas
- In-depth telemetry and reporting including automatic metrics, logs and traces for all traffic within a cluster, including cluster ingress and egress
Here's IBM's rationale for contributing to the development of Istio, as explained in a blog post today:
We continue to see an increasing number of developers turning to microservices when building their applications. This strategy allows developers to decompose a large application into smaller, more manageable pieces. Although decomposing big applications into smaller pieces is a practice we've seen in the field for as long as software has been written, the microservices approach is particularly well suited to developing large scale, continuously available software in the cloud.
We have personally witnessed this trend with our large enterprise clients as they move to the cloud. As microservices scale dynamically, problems such as service discovery, load balancing and failure recovery become increasingly important to solve uniformly. The individual development teams manage and make changes to their microservices independently, making it difficult to keep all of the pieces working together as a single unified application. Often, we see customers build custom solutions to these challenges that are unable to scale even outside of their own teams.
Google also weighed in on the project in its own blog post. "Istio encapsulates many of the best practices Google has been using to run massive-scale services in production for years," the company said. "We're happy to contribute this to the community as an open solution that works with Kubernetes; on-premises or in any cloud, to help solve challenges in modern application development. Istio provides developers and devops fine-grained visibility and control over traffic without requiring any changes to application code and provides CIOs and CSOs the tools needed to help enforce security and compliance requirements across the enterprise."
Istio is also a hot topic of discussion on Hacker News right now, where one commenter said: "This may be the most important project in distributed computing in a long time. It solves some fundamental problems that layer 3 networking has been unable to tackle. Its initial integration with Kubernetes is great but long term it could be the basis of all application level communication whether it is deployed in a container orchestration system, VMs, bare metal or as an enabler for Lambda (function) frameworks."
While the Istio 0.1 release will primarily introduce the project and get early feedback while providing a glimpse of future work, two more releases are in the works, according to a project roadmap.
Google also provided a peek at upcoming developments. "Today, you can manually install and use Istio on Google Container Engine; in the future, we intend to provide a more automated and integrated experience.
"We also intend to bring Istio capabilities to Cloud Endpoints and Apigee suite of products. This will provide common visibility and management for both APIs and microservices for organizations of any size. As we work with the community to harden Istio for production-readiness, we plan to provide deeper integration with the rest of Google Cloud."
Developers can see GitHub-hosted Istio code here. They can get started with Istio by starting with the project's Tasks functionality. A sample application is also available.
About the Author
David Ramel is an editor and writer at Converge 360.