News
Report: Security of iOS and Android Mobile Apps 'Roughly Equivalent'
- By David Ramel
- June 19, 2019
New research from security vendor Positive Technologies examines vulnerabilities and threats in mobile applications, stating that the security level of iOS and Android apps is "roughly equivalent between the two platforms."
General industry consensus has long been that Android apps are more vulnerable because of the OS's open architecture, popularity and other factors, but the new report jives with recent IDC research that found "no correlation between device OS types and frequency of mobile security incidents involved."
IDC seemed to indicate that media hype contributed to that aforementioned industry consensus, saying: "Reports in the media and blogosphere also create a negative perception around Android. News of the latest Android kernel exploits, with ominous-sounding code names -- Stagefright, QuadRooter, Dirty COW -- spread quickly. Whether a real threat or not, cumulative reports on the weakness of Android OS code and apps, or overall mistrust of software downloaded from Android app stores, can stick in the minds and perceptions of many IT decision-makers."
It should be noted, however, that the IDC research -- a whitepaper titled "Android for Enterprise: Digital Transformation Opportunity" -- was sponsored by Google, creator of Android.
The new "Vulnerabilities and Threats in Mobile Applications 2019" report by Positive Technologies, which provides enterprise security solutions, said "critical vulnerabilities are slightly more common in Android applications, compared to their iOS counterparts (43 percent vs. 38 percent). The experts categorize this difference as minimal: the security level of mobile apps is roughly equivalent between the two platforms."
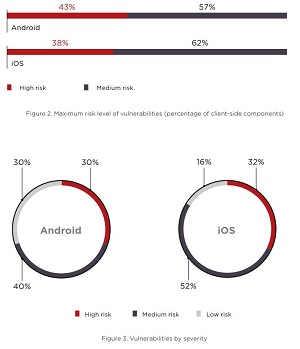 [Click on image for larger view.]
Security on Android, iOS (source: Positive Technologies)
[Click on image for larger view.]
Security on Android, iOS (source: Positive Technologies)
A news release detailed other highlights of the report:
- Insecure data storage was identified as the most common vulnerability. This flaw is found in 76 percent of mobile apps and in some cases could enable hackers to steal passwords, financial information, personal data, and correspondence.
- Of the vulnerabilities found, 89 percent could be exploited by malware. The risk of infection jumps on rooted and jailbroken devices, but malware can also elevate privileges by itself. Once on the victim's device, malware can ask for permission to access user data and, if permission is granted, the malware can send data to the attackers.
- The server side of applications (hosted by the developer and responsible for storing, processing, and synchronizing information) is just as weak as the client side: 43 percent of server-side components have a poor or extremely poor protection level. One third (33 percent) contain critical vulnerabilities. The most common high-severity vulnerabilities on the server side include insufficient authorization and information leakage.
The report itself delves into the technical details of security threats and vulnerabilities and contains many recommendations for developers to address the security issues, including:
- Use LocalBroadcastManager to send and receive broadcast messages not intended for third-party applications.
- If you need to use links for interaction between components, use universal links.
- To disable use of third-party keyboards within an application, implement the shouldAllowExtensionPointIdentifier method within the application's UIApplicationDelegate.
- Disable app from being backed up by setting the android:allowBackup directive to "false."
- Use a special background image to mask sensitive data on the application screen.
- Modern devices tend to use biometrics (Touch ID or Face ID) for authentication in applications. In this case, the PIN code is stored on the device. Local storage of sensitive data is acceptable only in special directories with encryption. Android has a key vault called Keystore; iOS has Keychain.
- It is not necessary to send one-time passwords twice in both SMS messages and push notifications. Instead, use the password delivery method selected by the user.
- TRACE can be used to bypass cookie protection with the httpOnly flag. Disable handling of TRACE requests.
- Limits on authentication attempts must be implemented both on the server side and on the client side.
- Filter user-entered data on the server side. Use HTML coding for special characters.
- Session lifetime must be limited. The session ID must be deleted both on the client side and on the server side. The server must create a new session for the user every time authentication is required.
- For maximum security of client–server communication, we recommend using certificate pinning. With this approach, the certificate is embedded directly in the code of the mobile application. As a result, the application becomes independent of the OS certificate store. This prevents MITM [man in the middle] attacks.
Positive Technologies exec Leigh-Anne Galloway said: "In 2018, mobile apps were downloaded onto user devices over 205 billion times. Developers pay painstaking attention to software design in order to give us a smooth and convenient experience and people gladly install mobile apps and provide personal information. However, an alarming number of apps are critically insecure, and far less developer attention is spent on solving that issue. Stealing data from a smartphone usually doesn't even require physical access to the device."
About the Author
David Ramel is an editor and writer at Converge 360.