News
Open Source Security Audit 'Should Be a Wake-Up Call'
- By David Ramel
- May 1, 2017
For at least nine years, ADTmag has been reporting open source security issues, and two studies within the past couple weeks demonstrate the problems are persisting.
Last week, this site reported on a study conducted by German researchers that linked open source software vulnerabilities to developers copying source code from flawed online tutorials and pasting it into open source applications.
Coincidentally, Black Duck Software Inc. recently revealed the results of security audits it undertook that show "widespread weakness in addressing open source security vulnerability risks."
The company's Center for Open Source Research & Innovation (COSRI) last year conducted 1,071 source code audits -- mostly associated with mergers and acquisitions -- and discovered that more than 60 percent of the applications it examined contained open source security vulnerabilities.
"Open source use is ubiquitous worldwide and recent research reports show that between 80 percent and 90 percent of the code in today's apps is open source," Black Duck CEO Lou Shipley said in a statement publicizing the results of the company's "2017 Open Source Security & Risks Analysis."
"This isn't surprising because open source is valuable in lowering dev costs, accelerating innovation and speeding time to market. Our audits confirmed the universal use, but also revealed troubling levels of ineffectiveness in addressing risks related to open source security vulnerabilities and license compliance challenges."
The financial industry contained an average of 52 open source vulnerabilities per application, while 60 percent of the applications contained high-risk vulnerabilities, the company said. It added: "The retail and e-commerce industry had the highest proportion of applications with high-risk open source vulnerabilities, with 83 percent of audited applications containing high-risk vulnerabilities."
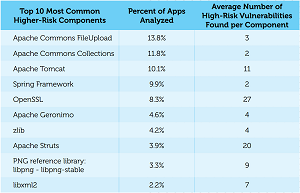 [Click on image for larger view.]
The Main Offenders (source: Black Duck Software)
[Click on image for larger view.]
The Main Offenders (source: Black Duck Software)
The high number of open source security issues arises from the widespread use of open source software itself, components of which were found in 96 percent of the audited apps, said Black Duck, which emphasized the preponderance of license compliance problems as a prime contributor.
"Open source license conflicts were widespread," the company said. "The audited applications contained 147 open source components on average -- a daunting number of license obligations to keep track of -- and in fact 85 percent of audited applications contained components with license conflicts. The most common challenges were GPL license violations, with 75 percent of applications containing components under the GPL family of licenses, but only 45 percent of those applications in compliance with GPL obligations."
Other key data points of the audits include:
- 67 percent of analyzed applications using open source had vulnerabilities in the components used.
- On average, apps contained 27 open source vulnerabilities.
- On average, vulnerabilities identified in these applications have been publicly known for over four years.
- Risky versions of components such as Apache Tomcat and OpenSSL were commonly found across industries.
- Even versions of Linux Kernel, PHP, MS .NET Framework and Ruby on Rails were found to have vulnerabilities.
Part of the problem, Black Duck said, is that using open source software puts the onus for security squarely on developers or users who leverage community contributions.
"Unlike commercial software, where updates are automatically 'pushed' to users, open source has a 'pull' support model -- users are responsible for keeping track of vulnerabilities as well as fixes and updates for the open source they use," the audit report said.
In light of the continuing open source security problem, Black Duck advised organizations to:
- Fully inventory open source software.
- Map open source to known security vulnerabilities.
- Identify license and quality risks.
- Enforce open source risk policies.
- Monitor for new security threats.
"Reading this report should be a wake-up call," said company exec Chris Fearon. "Everyone is using lots of open source, but as the audits show, very few are doing an adequate job detecting, remediating and monitoring open source vulnerabilities in their applications. The COSRI analysis of the audits clearly demonstrate that organizations in every industry have a long way to go before they are effective in managing their open source."
About the Author
David Ramel is an editor and writer at Converge 360.