News
Researchers: Open Android Ports Leave Millions Vulnerable
- By David Ramel
- May 3, 2017
As if there weren't already enough security problems for mobile app developers to worry about.
Researchers at the University of Michigan have published a paper in which they break new ground in investigating security implications of open Internet ports in Android applications, finding flawed apps that leave millions of users vulnerable to attack.
They developed a tool called OPAnalyzer to analyze open Internet ports on Android apps. Such ports are used widely in more traditional client/server scenarios and have recognized security attack vectors that are addressed through such means as firewalls and user authentication. On the mobile front, however, things are different because of factors such as the frequent inability to maintain stable IP addresses, among several others.
To get a comprehensive handle -- apparently for the first time -- on the "under-explored" mobile side of things, the researchers analyzed thousands of Android apps.
"We find that nearly half of the usage is unprotected and can be directly exploited remotely," the paper said. "From the identified vulnerable usage, we discover 410 vulnerable applications with 956 potential exploits in total. We manually confirmed the vulnerabilities for 57 applications, including popular ones with 10 to 50 million downloads on the official market, and also an app that is pre-installed on some device models. These vulnerabilities can be exploited to cause highly-severe damage such as remotely stealing contacts, photos, and even security credentials, and also performing sensitive actions such as malware installation and malicious code execution."
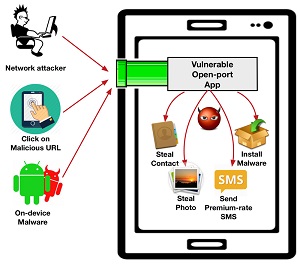 [Click on image for larger view.]
Open Port Attack Vectors and Targets (source: University of Michigan)
[Click on image for larger view.]
Open Port Attack Vectors and Targets (source: University of Michigan)
The UM team considered the following three adversary types:
- Malware on the same device. A malicious app, or malware, installed by the smartphone user can use
netstat command or proc file /proc//net/tcp to find the listening ports on the same device and send exploitation traffic.
- Local network attacker. For victims behind NAT [network address translation] or using private WiFi networks, attackers sharing the same local network can use ARP scanning to find reachable smartphone IP addresses at first, and then launch targeted port scanning to discover vulnerable open ports.
- Malicious scripts on the Web. When a victim user visits an attacker-controlled Web site using their mobile device, malicious scripts running in the handset's browser can exploit the vulnerable open ports on the device by sending network requests, which doesn't require any permission.
Although the researchers were breaking new ground in their systematic analysis of open port security vulnerabilities, such attack vectors have actually resulted in real-world damage, such as the flawed Moplus SDK from Chinese Web services company Baidu. That resulted in a "wormhole" that put some 100 million Android users at risk, according to a 2015 International Business Times article that reported on the threat, first identified by security company Trend Micro.
New exploits were discovered by the team, though, including information leakage, denial of service, and privileged execution.
The team categorized three open port usage scenarios -- intended for use by app users, intended for back-end communication and intended for local communication -- and proposed mitigation strategies for each.
Also, a Web site was set up for the project, which includes demonstrations of various attacks, including videos.
The "Open Doors for Bob and Mallory: Open Port Usage in Android Apps and Security Implications" paper was published by Yunhan Jack Jia, Qi Alfred Chen, Yikai Lin, Chao Kong and Z. Morley Mao.
About the Author
David Ramel is an editor and writer at Converge 360.